Digital Debut
HIPAA Biannual Update
January to June 2025
BY MAIA KUNKEL | SEPTEMBER 15, 2025
During the first half of 2025, healthcare organizations across the country posted 330 breaches of protected health information (PHI) affecting 500 or more individuals. Consistent with previous updates, rises in unauthorized access or hacking comprised almost all—98 percent—of the breaches. The percentage of breach investigations due to improper disposal, loss, theft, or unauthorized access or disclosure of PHI continues to decrease. For the first time since 2023, loss of PHI was not cited as a cause of a breach investigation.
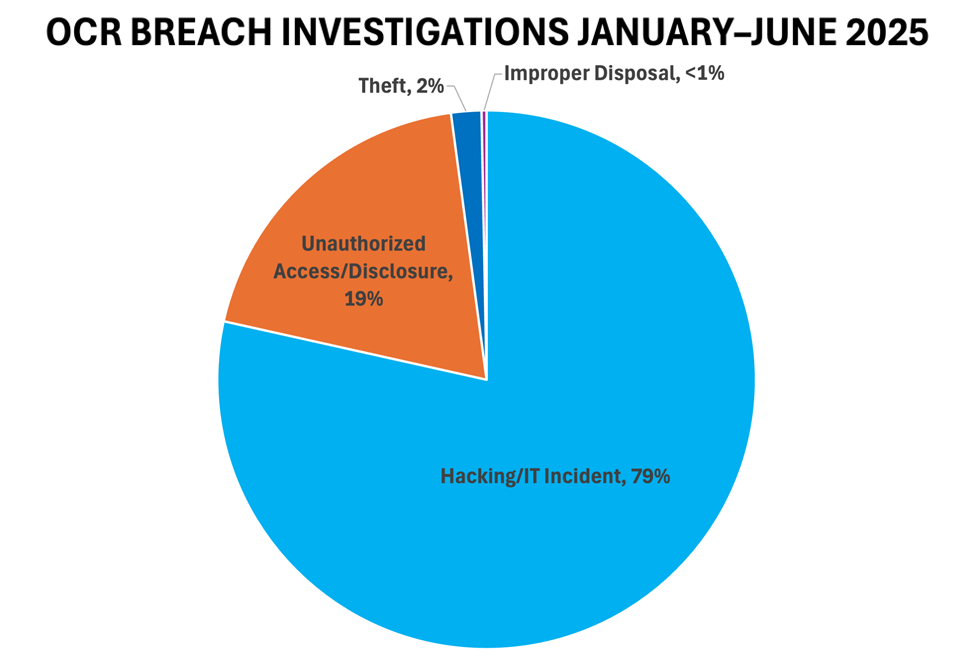
SOURCE: ASCA
Within the Department of Health and Human Services (HHS), the Office for Civil Rights (OCR) is the enforcement agency responsible for protecting rights related to health information privacy. This includes enforcement actions for violations of the Health Insurance Portability and Accountability Act of 1996 (HIPAA), which delineates who can view or receive an individual’s PHI and sets standards for security of PHI when being stored or transferred electronically.
ASCs can take important steps to help prevent breaches and limit their liability. They can review and update policies and procedures frequently to help prevent unauthorized access, improper disposal, loss and theft of PHI. ASCs also can visit the OCR website to review enforcement actions and consider how they can avoid the mistakes made by others.
Many recent enforcement actions have been through the HIPAA Right of Access Initiative, which is an enforcement effort established through HIPAA to ensure that patients can access their health information from their healthcare providers. In the first half of 2025, OCR has announced two more settlements in this initiative, bringing the total to 53 enforcement actions since 2019. The recent investigations found varying degrees of noncompliance with patients’ requests to promptly receive their medical records and resulted in settlements of up to $200,000. Two examples of recent resolution agreements are provided below, along with precautions ASCs can take to avoid similar violations.
What happened: OCR began investigating the public academic health center and research university in January 2021 after receiving a second complaint from an individual’s personal representative alleging that the individual was not given all their requested records. In September 2020, OCR resolved the first complaint after notifying OHSU of potential noncompliance. OHSU did not provide all the requested records until August 2021, nearly 16 months after the first request. In December 2024, OCR imposed a $200,000 civil monetary fine for OHSU’s failure to take timely action in response to the patient’s right of access request.
Takeaways for ASCs: In 2019, OCR introduced a specific provision of the HIPAA Privacy Rule related to health information technology (HIT) to help enforce and support individuals’ right to timely access their health records at a reasonable cost. ASCs should review their policies and training programs to ensure that they are able to meet all HIPAA obligations when a patient requests access to their medical records. As OCR continues to announce more settlements in its HIPAA Right of Access Initiative, ASCs should keep in mind that it remains critical that patients are able to access their own medical information in a timely manner and be able to promptly take charge of healthcare decisions.
What happened: PIH, a California healthcare network, filed a breach report in January 2020. The report stated that in June 2019, a phishing attack compromised 45 of its employees’ email accounts. The attack resulted in a breach of more than 189,000 individuals’ PHI, including names, Social Security numbers, diagnoses and financial information. OCR’s investigation found multiple potential violations of the HIPAA rules, including the failure to conduct an accurate and thorough risk analysis and the failure to notify affected individuals and the media of a breach of unsecured PHI within 60 days of discovery. PIH agreed to pay a $600,000 monetary fine and implement a corrective action plan with two years of monitoring by OCR.
Takeaways for ASCs: Hacking and ransomware have quickly become the most pressing cyber threat in healthcare. Since 2018, OCR has received a 264 percent increase of reported large breaches involving ransomware and a 256 percent increase in reported hacking incidents. ASC staff and patients alike should be confident that electronic PHI (ePHI) is secured and inaccessible from bad actors, both internally and externally. While the task of safeguarding PHI in an increasingly targeted sector might feel onerous, OCR has shared several strategies that all healthcare entities covered by HIPAA, including ASCs, can implement now to strengthen their defenses.
- Review all vendor and contractor relationships to ensure business associate agreements are in place, as appropriate, and address breach or security incident obligations.
- Integrate risk analysis and risk management into business processes, conducted regularly and when new technologies and business operations are planned.
- Ensure audit controls are in place to record and examine information system activity.
- Implement a regular review of information system activity.
- Utilize multifactor authentication to ensure only authorized users are accessing ePHI.
- Encrypt ePHI to guard against unauthorized access.
- Incorporate lessons learned from incidents into the overall security management process.
- Provide regular training specific to organization and job responsibilities and reinforce staff members’ critical role in protecting privacy and security.
To help ASCs remain compliant with HIPAA, ASCA provides the HIPAA Resource page that can be found in the federal regulations section of ASCA’s main site. It provides background on the act itself, as well as the four key provisions: privacy, security, enforcement and breach notification.
Write Maia Kunkel at mkunkel@ascassociation.org with questions.